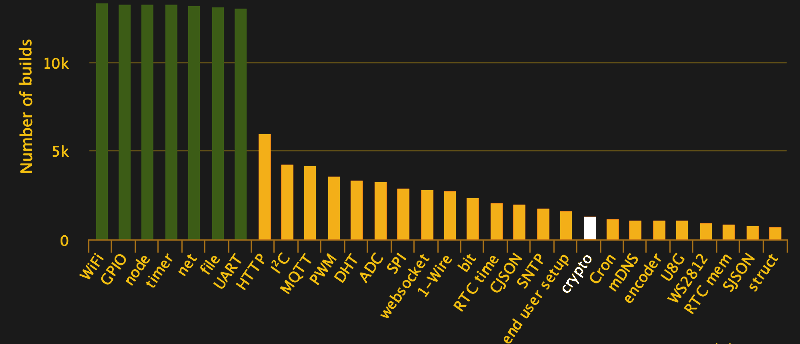
5. How to use Security Functions — Android Application Secure Design/Secure Coding Guidebook 2022-01-17 documentation

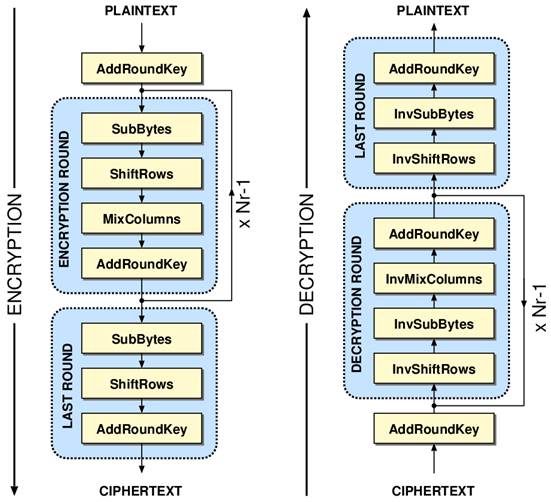
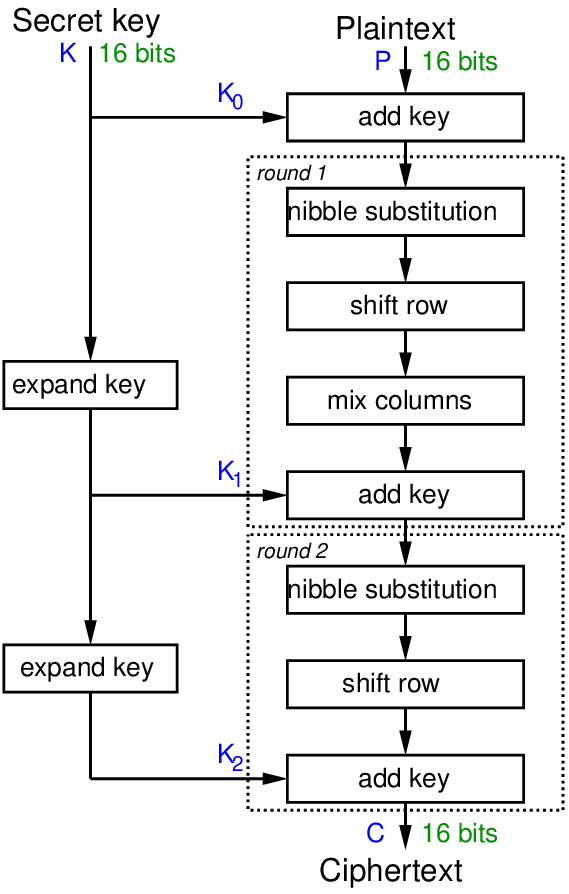
An Introduction to the Advanced Encryption Standard (AES) | by Adrienne Domingus | The Startup | Medium
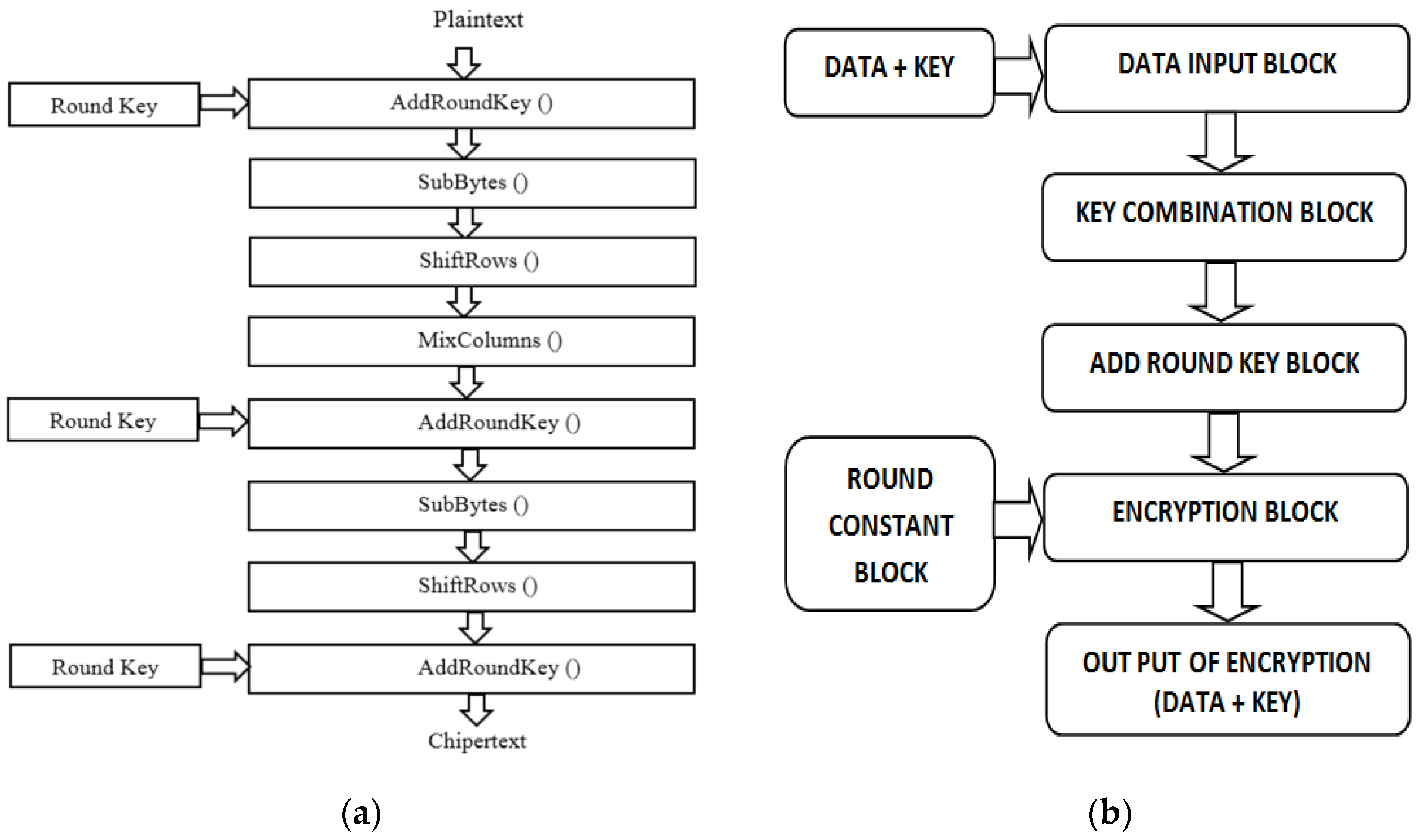
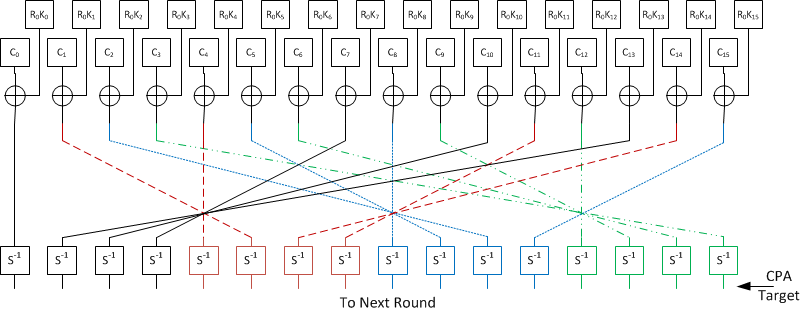
Electronics | Free Full-Text | 10 Clock-Periods Pipelined Implementation of AES-128 Encryption-Decryption Algorithm up to 28 Gbit/s Real Throughput by Xilinx Zynq UltraScale+ MPSoC ZCU102 Platform | HTML